NDR: Integration Guide - Windows Servers
Description
The Windows Server Sensor (agent) runs as a Windows service in a compatible Windows Server system. The Server Sensor observes events within the Windows Server system and sends Interflow data records to the data processor.
The captured events are:
Hardware
Security
System
Windows Firewall
Windows Defender
PowerShell
File Integrity Monitoring (if enabled in the Sensor Profile)
The Windows Server Sensor provides the following key capabilities:
If the sensor has coverage over the domain controller, Stellar Cyber enriches data with the relationship between users and IP addresses.
If the sensor has coverage over the DHCP server, Stellar Cyber sees the relationship between hostnames and IP addresses, and so can track assets when the IP address changes.
Windows Server Sensor provides the data foundation for Stellar Cyber's machine learning alerts that use the Windows Events index.
Although you can also provide coverage of Windows logs using other visibility tools such as the ManageEngine Log Collector or Winlogbeat, the logs provided by these tools are not normalized, enriched, and stored in the Windows Events index used for machine learning alert generation (except for ManageEngine ADAudit Plus logs) and cannot be used for machine learning alert generation.
In addition, the Windows Server Sensor provides the following advantages over alternative solutions:
Windows Server Sensor provides easier deployment and maintenance.
Windows Server Sensor provides granular filtering at the edge through the Stellar Cyber user interface.
By using the Windows Server Sensor, you do not need to deploy another modular sensor to forward logs from ManageEngine or Winlogbeat.
*** PLEASE PLEASE PLEASE read the instructions and pay attention to any bold, colored, outlined or other text within boxes like this!!! ***
Text that is bold, colored, outlined, or within a box like the above is important. This is done as most of the time it will answer commonly asked questions or is information critical to the configuration. Failure to pay attention to this might result in the configuration not working or other delays in your implementation.
Information
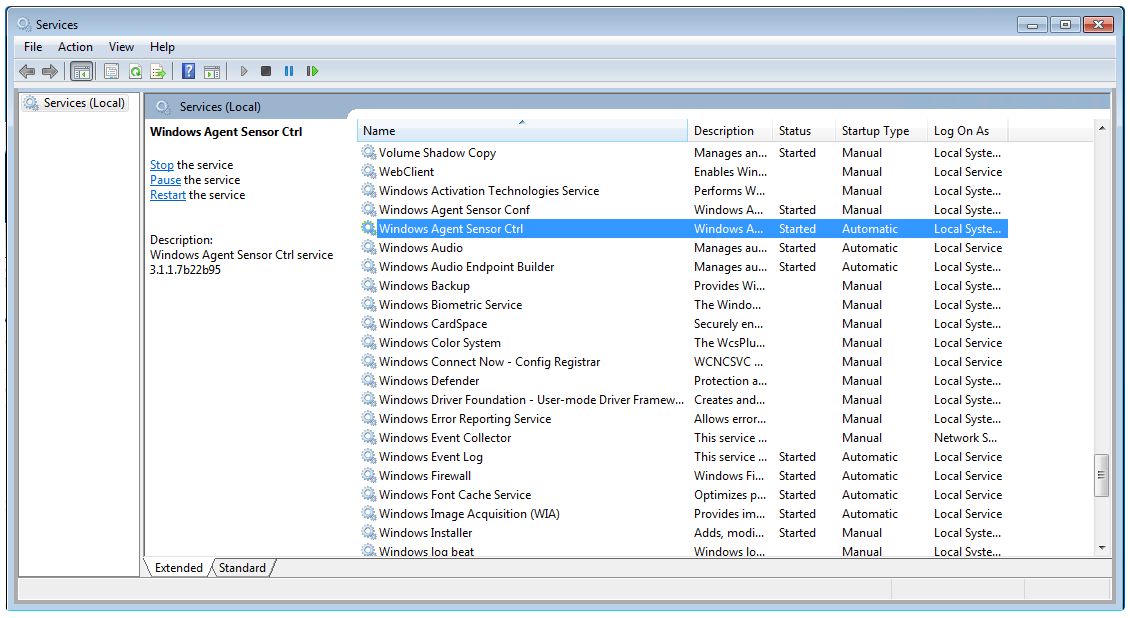
Windows Server Sensor Processes
The Windows Server Sensor launches the following processes:
Name in Task Manager | Name in Services App | Description |
|---|---|---|
aella_conf_win_srv.exe | Windows Agent Sensor Conf | Handles Windows Server Sensor configuration |
aella_ctrl_win_srv.exe | Windows Agent Sensor Ctrl | Monitors other services, and can stop or start them based on the configuration |
aella_diagnostics_win_srv.exe | Windows Agent Sensor Phonehome | Sends Windows Server Sensor logs to DP |
aella_winlog.exe | Windows Agent Sensor Logbeat | Sends Windows events to DP |
aella_filebeat.exe | Windows Agent Sensor Filebeat | Sends log files from Windows DHCP server (if installed and running) to DP |
aella_fim.exe | Windows Agent Sensor FIM | Provides file integrity monitoring services, as configured in the Sensor Profile |
Exclude Server Sensor from AV/EDR Scanning
Stellar Cyber recommends that you prevent potential conflicts by configuring any anti-virus or EDR software installed on the same host as the Server Sensor to exclude the Server Sensor installation directories from scanning. The directories to exclude are as follows:
Server Sensor Type | Folders/Files to Exclude from AV/EDR Scanning |
|---|---|
Windows | C:\ProgramData\Stellarcyber C:\Program Files\Aella C:\Windows\Stellar_syswatcher.exe (sensors running pre-4.2.2 versions) |
Possible False Positives from FireEye PROCGUARD
During installation of the Windows Server Sensor, it is possible that FireEye PROCGUARD may report the following alert – Attempted LSASS access by aella_conf_win_srv.exe detected. After investigation, Stellar Cyber has determined that this is a false positive and that the aella_conf_win_srv.exe service does not interact with C:\\Windows\\system32\\lsass.exe on the host machine.
About Sysmon in this Release
Unlike previous Window Server Sensor releases, releases from 4.2.2 onwards do not download and install the stellar_syswatcher (Microsoft Sysmon64) service due to potential system crashes in certain older operating systems (Windows 2008R2 and 2012, although possibly others).
Note the following:
Upgrades of Windows Server Sensors leave the existing version of stellar_syswatcher intact and do not upgrade it. You can continue to use the existing Sysmon service safely.
You can install the latest version of Sysmon (v13.31 at this writing) manually if you want the Windows Server Sensor to report Sysmon events to the DP. This is recommend for improving visibility on Windows systems. However, Stellar Cyber strongly recommends that you test your installation in a non-production environment to verify operations before moving to production.
Supported Systems
The Windows Server Sensor is supported on Windows Server 2008 R2 and later. The Server Sensor is only available in 64-bit.
When the system sleeps, the connection drops, and no data is collected. The connection is re-established when the system wakes. To avoid this, configure Windows to Never sleep.
The host Windows Server into which the Windows Server Sensor is installed must meet the following minimum requirements, regardless of whether it is a physical or virtual server:
Component | Specification |
|---|---|
Host CPU | Xeon Core 2 virtual cores (2.0 GHz or more) |
Host RAM (GB) | 8 |
Host SSD (GB) | 128 |
OS | Windows Server 2008 R2 (or later) |
Update Windows Server Software Before Installing Windows Server Sensor
It's a good idea to use Windows Update to make sure your Windows Server software is up to date before installing the Windows Server Sensor. For example:
The Windows Server Sensor software includes the AI_ChainedPackageFile.vc_redist.x64.exe redistributable from Microsoft. Successful installation of this redistributable requires the following prerequisites from Microsoft, installed either in the order below or as part of a standalone package (KB2919355 is a prerequisite of KB2999226).
PowerShell Requirements for 4.3.x Releases
Depending on the Windows Server Sensor version you are installing or upgrading to, PowerShell may or may not be required:
Starting with the 4.3.4 release, PowerShell is no longer required for Windows Server Sensor installs or upgrades.
You can perform a clean installation of the 4.3.4+ Windows Server Sensor on a target system without PowerShell installed.
The 4.3.1, 4.3.2, and 4.3.3 versions are all supported for direct upgrades to 4.3.4+. Each of these versions required PowerShell for its initial installation. You can still upgrade these versions directly to 4.3.4+ even if PowerShell was removed after the 4.3.1/4.3.2/4.3.3 sensor was installed.
If you must perform an interim upgrade to a pre-4.3.4 version before upgrading to 4.3.4+, PowerShell must remain installed until the version to which you are upgrading no longer requires it (4.3.4 and later)
For all pre-4.3.4 versions, the host Windows Server must be running PowerShell 2.0 or greater. In nearly all cases, a supported Window Server version will already have a version of PowerShell installed by default that meets this requirement. If for some reason, however, your Windows Server is not running PowerShell 2.0 or greater (for example, due to a Windows Group Policy Objects exclusion), the Server Sensor installation will fail with details in the installation logs.
Step 1: Firewall Configuration
The Linux Server Agent requires specific ports & URLs to be open on your firewall for outbound communication:
Port | Protocol | Explanation |
|---|---|---|
53 | TCP & UDP | For DNS resolution |
123 | UDP | For NTP synchronization |
6640-6648 | TCP | For communicating with the DP |
8443 | TCP | For software and file downloads from the DP |
8888-8889 | TCP | Receiver ports for communicating with the data analyzer |
Step 2: Server Configuration
Obtaining the Windows Server Sensor Installer
The Server Sensor is distributed as an MSI file.
The software can be downloaded from the production server directly by using the following URL.
For 64-bit Windows: Stellar windows-x64 5.1.1.msi.
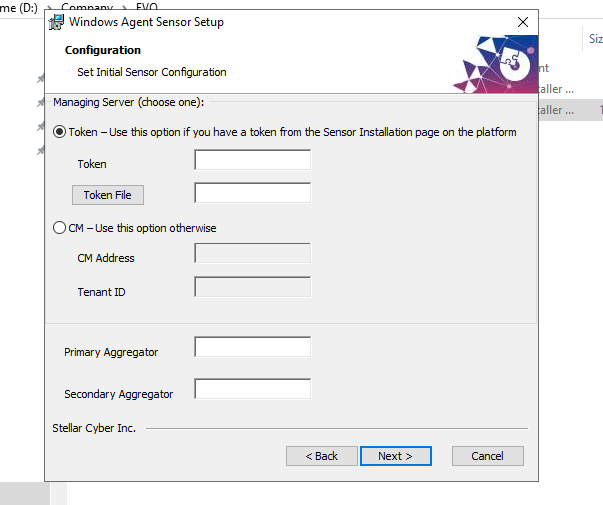
Agent Installation
Step 3: Data Verification
Once the agent is installed:
Reply to your ticket with the server’s Hostname and IP address (private) of the server so it can be authorized and have the correct profile applied.
Uninstalling the Server Sensor
Stellar Cyber recommends that you remove the Windows Server Sensor using the Change button in the Programs and Features control panel instead of the Uninstall button.
Using the Change button gives you access to the following additional uninstall options that ensure the program and all its data are removed completely:
Remove Data Files
Remove Scheduler Task
If you are planning on reinstalling a 4.2.2+ Windows Server Sensor, Stellar Cyber recommends that you leave these items unchecked.
If you want to uninstall completely, you should check these boxes.
During the uninstallation, a Windows command prompt window may appear. Do not close this window manually – it closes automatically when the uninstallation is complete.
Related Pages
- NDR: Deploying a Virtual Sensor in AWS
- NDR: Integration Guide - Physical Sensor Deployment
- NDR: Integration Guide - Linux Servers
- NDR: Integration Guide - Syslog Port Index
- NDR: Integration Guide - Windows Servers
- NDR: Integration Guide - Firewall Syslog Forwarding
- NDR: Deploying a Virtual Sensor in Hyper-V
- NDR: Sensor Configuration & Authorization
- NDR: Deploying a Virtual Sensor in GCP
- NDR: Virtual Sensor Requirements
- NDR: Deploying a Virtual Sensor in Azure
- NDR: Deploying a Virtual Sensor in OCI
- NDR: Deploying a Virtual Sensor in VMware
- NDR: Deploying a Virtual Sensor in KVM
Information & Recommendations provided for reference only. By using any information provided, you are agreeing to our Terms and Conditions.